Shadow IT: How to Track Hidden Systems
The IT department can only protect what they know. This makes unrecorded systems an incalculable security risk. The good news: With an automated inventory, so-called shadow IT can be tracked down in no time.
The IT department can only protect what they know. This makes unrecorded systems an incalculable security risk. The good news: With an automated inventory, so-called shadow IT can be tracked down in no time.

Shadow IT includes all IT systems such as apps, cloud software, networked devices, etc. that exist outside a company's official IT infrastructure and without the knowledge of the IT department. These can be Software as a Service (SaaS) applications used by employees without the permission of IT management. Or old websites that have been forgotten and should have been shut down long ago. This also includes arbitrarily installed productivity and collaboration platforms, provided they are not subject to IT control.
Undetected systems contribute significantly to the attack surface of the IT infrastructure. They are left out of protection and security measures because the IT department is not aware of their existence
Since IT administrators are usually unaware of the extent of enterprise-wide shadow IT, they cannot monitor it, let alone protect it. The systems remain unattended in the IT infrastructure yet still reachable on the internet - a welcome gateway for cybercriminals.
As an employee, think of the number of times you've gone online and installed an application or connected a printer or Webcam to your company device. Can you imagine how many unrecorded systems accumulate over the years in an organization with many hundreds or thousands of employees? Every account that an employee sets up with his or her company email address opens up a new entry point to the network. Passwords are readily used repeatedly, making it easier for hackers. Any external device that connects to your network is an access point. As long as these devices are not part of the company's IT inventory, they are not monitored.
Attack vectors or entry points that are not even known to your IT department can be the most trivial little thing and, in the worst case scenario, can cause your entire IT infrastructure to fall into the hands of IT criminals.
With a vulnerability analysis, the dreaded shadow IT can be found in the shortest possible time. In the first step, the systems accessible via the Internet are identified and inventoried based on their IP addresses. The next step is to check for IT security.
We ourselves are always surprised by what we find on the web - it's all there: For example, IOT devices like an automotive supplier's factory floor surveillance camera that transmitted images of the prototype to the Internet or old, unpatched websites that no one knows about anymore, but are still accessible from the internet. Unintentionally publicly accessible development apps and GIT directories also turn up frequently.
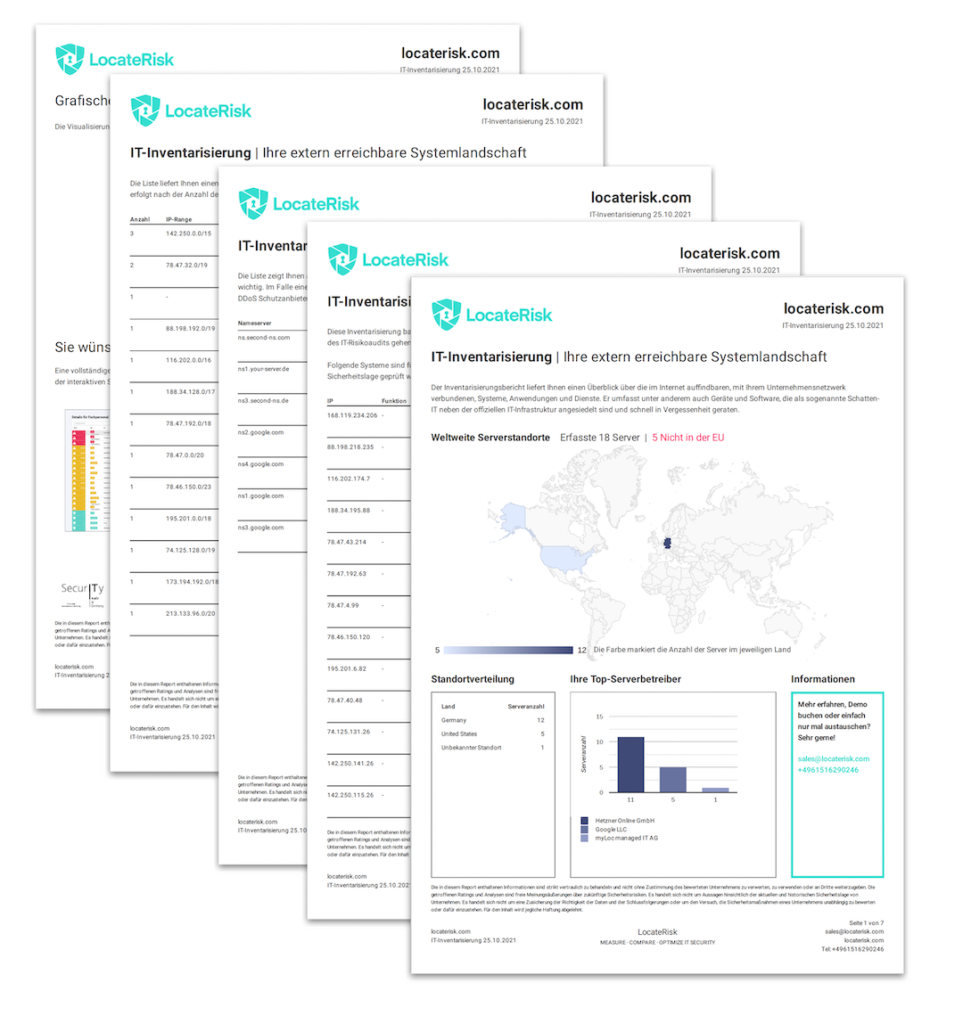
The first step in dealing with shadow IT is to know that it exists. An automated IT inventory provides the necessary overview in the shortest possible time. Looking the other way and not knowing is not an alternative. By doing so, you play into the hands of attackers. On the other hand, if you have an overview of your systems and their security status, you can initiate measures and close potential entry points.
For companies that want to gain an overview of their existing network devices and systems: A LocateRisk IT inventory is free of charge and ready in less than 5 minutes.
Just send an email to em@LocateRisk.com send
Identify and reduce your cyber risks through a comparable and understandable overview of your IT security. Let our experts advise you and find out how LocateRisk can help you solve your cyber risks.