IT risk analyses for SOC, SIEM, SOAR and ticketing
Increase your turnover with extended SOC services
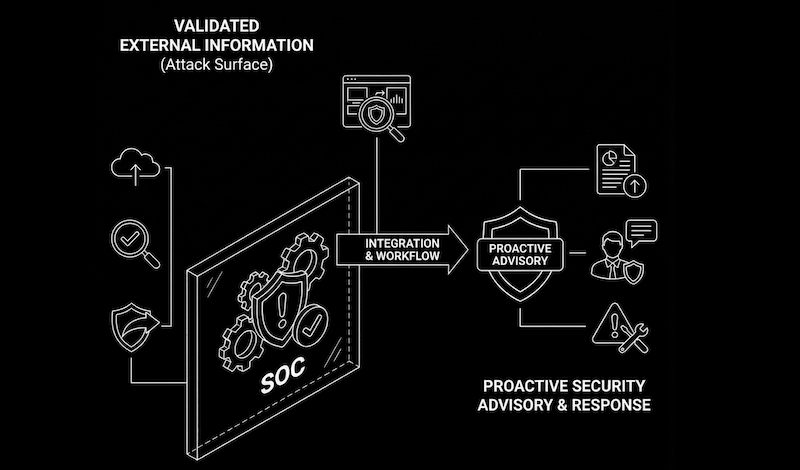
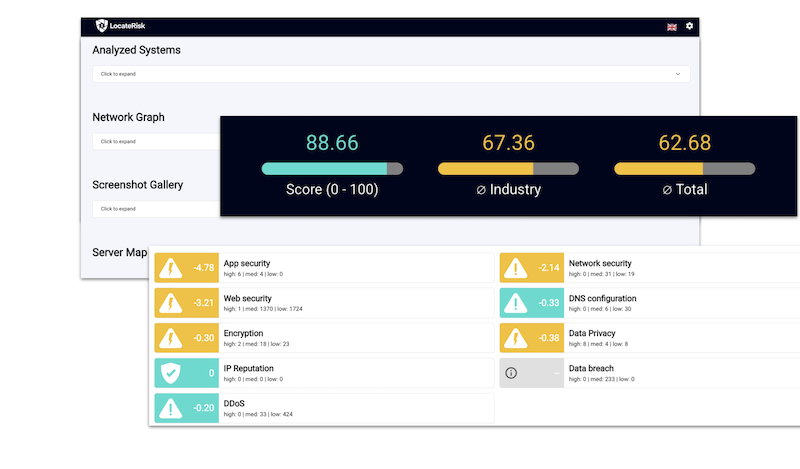
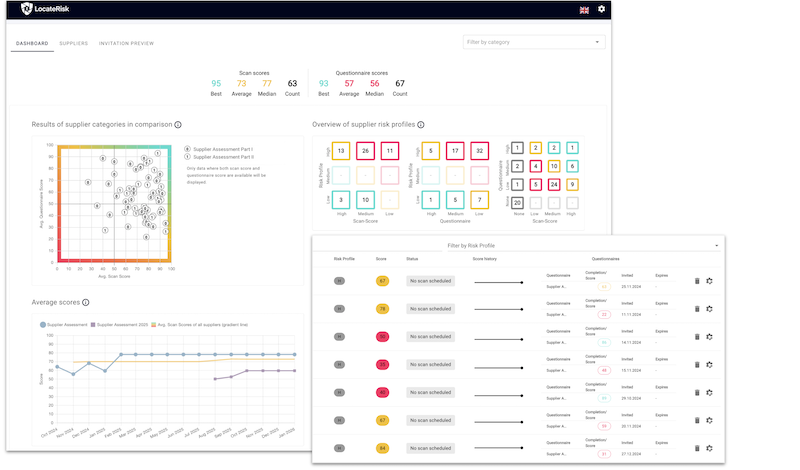
LocateRisk enhances your SOC with continuous information about current risks in the external IT infrastructure. The technology automatically identifies the systems and allows recurring checks of the entire ecosystem: company + suppliers. The scan data can be integrated into existing SOC architectures and supports the implementation of relevant regulatory and normative requirements such as NIS-2, GDPR, ISO 27001, TISAX or DORA.