
EU Directive NIS2 Now Official
Learn who is affected, what's changing, and how we're helping you meet the requirements today.

How to Minimize the Ransomware Attack Risk
Ransomware attacks are a threat to business and society. All the more important to be able to minimize the risks continuously.

New Partnership with Aphos
NEWS UPDATE! We are happy to have a new, strong partner at our side with Aphos - Gesellschaft für IT-Sicherheit.
How Secure Is Your Cloud Environment?
Good to know: Cloud services are not a standard model for IT security. Because, as is so often the case in life, the same applies here: It all depends ...
IT Security and the Supply Chain Act: What to Do Now
The focus of the Supply Chain Act is on sustainability and human rights. But the topic of cybersecurity is also becoming relevant. Find out what you can already do today.

Shadow IT: How to Track Hidden Systems
Forgotten systems in the corporate network quickly become a gateway for attackers. Learn what shadow IT is and how to easily detect the systems.
E-Mail Security with SPF, DKIM and DMARC
SPF, DKIM and DMARC are standards to contain spoofing and pishing attacks. The record is quickly made. We show you how to do it.

Log4j Vulnerability - Find out Which of Your Servers Are Affected
Security vulnerability in Log4j - attacks are already underway. Do not waste time and check the security of your systems.

Statistic on IT Security: Hessian Municipalities
IT security experts have long warned about the cyber risks in public administrations. The problems are well known. The results are still lacking.
IT Security Statistics: The Parties
What is the state of cybersecurity in Germany? What is the situation like among the parties? Our survey shows that there is still a lot of room for improvement.
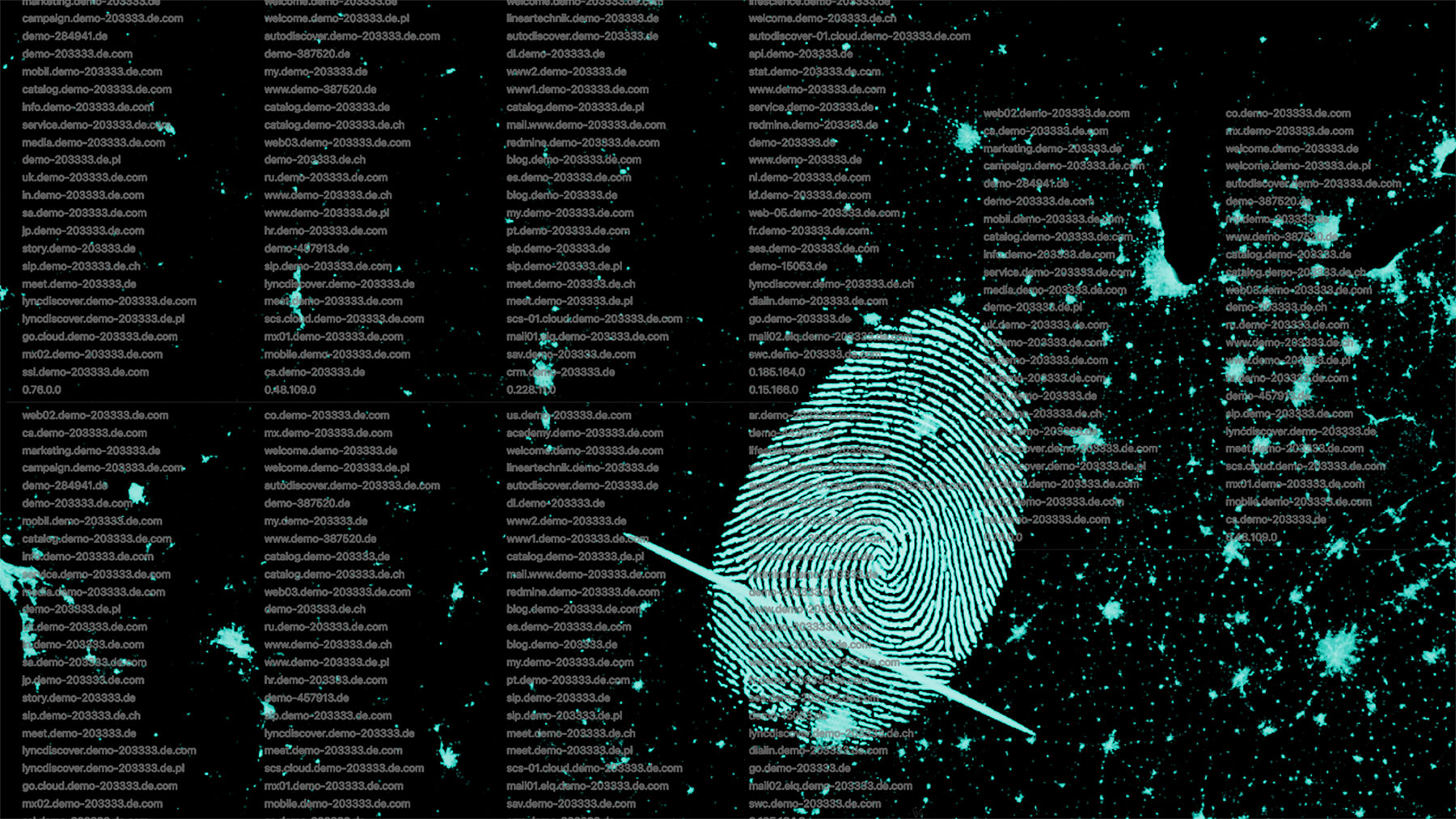
How You Can Increase Your IT Security with Automated Monitoring
Increasingly sophisticated, automated cyberattacks are driving up the resource and cost expenditures for IT security. This makes it all the more important for IT managers to be able to prove the effectiveness and profitability of their investments in attack prevention. This requires that they are able to efficiently assess the company-wide IT security status and communicate the result to the management level in a comprehensible manner.
The Digital Footprint: A Walk through the WWW
Whether it's a social media post, a quickly sent e-mail or a click made online: All of this leaves traces on the internet that reveal a lot about you...

Why Data Protection Is Essential in Cybersecurity
With the increasing relevance of cyber security, the topic of data protection automatically comes to the fore. Those who do not consider the topic extensively and optimize their website accordingly must expect sanctions.
Social Hacking, Cyber Espionage and Co.
Cybercrime will play an increasingly important role in the future. Especially for companies. And only those who know their adversaries can better protect their companies. This makes it all the more important to know the technologies used by attackers and to understand how they work. In Germany alone, attacks run into the high six-figure range every day - and the trend is rising. The speed at which attacks are carried out and the focus of the attackers are changing. For example, at 190 GBit per second, it is no longer just operating systems or browsers that are attacked, but also chips, processors and surveillance cameras, among other things.


