IT Security Statistics: The Parties
Survey 1st half of 2021. The data situation is more than serious! Unfortunately, it reflects exactly what many companies and public authorities have already had to experience. IT security precautions - where they exist - are not sufficient. The risk of becoming a victim of a cyber attack is increasing. Reason enough to take a closer look at the current IT security situation in Germany. To coincide with the upcoming federal elections, we start with the nine parties in the Bundestag.
IT risk analysis of the parties with seats in the German Bundestag
In view of the Bundestag elections, the National Research Center for Applied Cybersecurity, which is part of the Fraunhofer Gesellschaft, had ATHENE At the end of 2020, the IT systems of German political parties underwent an audit and serious vulnerabilities were identified. In addition, there was an offer of support and advice from Arne Schönbohm, head of the Federal Office for IT Security (BSI), on protection against cybercriminals. The WirtschaftsWoche reported on this in an article in July 2021.
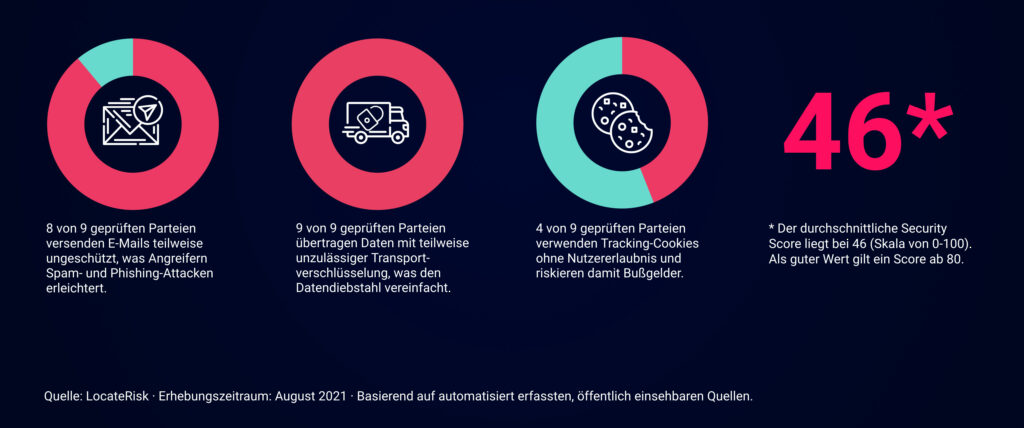
We wanted to know what the security situation is today and analyzed the IT attack surface of the nine Bundestag parties in August from an external perspective. This involved recording the systems that could be identified in the network and non-invasively checking their security-critical locations. In eight categories, based on publicly available government and industry standards. The results surprised us. The average security score was 46 on a scale of 0 to 100. A score of 80 or higher is considered adequate IT security.
IT security situation insufficient
When it comes to cybersecurity, there is still a lot of room for improvement among the parties in the Bundestag. Here are excerpts from three categories where action is needed and what role this plays in security.
First: Cybersecurity when sending mail
How well is the parties' mail service protected against identity theft? Can masses of spam e-mails be sent in their name - for example, to tap sensitive data? Unprotected mail dispatch enables spam and pishing attacks in the name of the party domain(s). If these are successful, attackers can gain access to further systems and infect them with malware. DNS configurations that can promote security-critical problems were found in 89 percent of the parties checked. We therefore recommend that all IT managers check the security settings at their domain providers.
Second, cybersecurity in data transport
Is the data flow between party employees and communication or business partners secured against access by third parties? In this category, the encryption quality of the data connections is evaluated. The validity and version of the security certificates and their correct implementation are also checked. The audit revealed that all parties transmit data with partially inadmissible transport encryption and have a clear need for optimization. This is because the insecure transmission of sensitive content on the network makes data theft easy and endangers the security of the parties as well as that of the networked companies.
Third: Data protection breaches
Are there any violations of the Basic Data Protection Regulation by the parties? The General Data Protection Regulation (GDPR) places personal data under special protection. These are processed whenever names, (IP) addresses, bank details, health data, location data and much more are collected from website visitors. In this category, we analyzed all identified party websites for basic GDPR violations. In 44 percent of the parties, borderline situations were discovered with regard to the GDPR that require manual review. As a reminder: Illegally set cookie banners and marketing, tracking or affiliate cookies are subject to warning letters and high fines.
Conclusion: Dear parties - We have to talk!
Based on the indications provided by ATHENE months ago, we had hoped that the analysis results would be at least halfway satisfactory at the time of the election. Now it turns out that there is still - or once again - a need for action. For this reason, we would also like to offer our support and are happy to provide the respective IT managers with the corresponding analysis for accelerated vulnerability remediation.