Smart implementation of supplier cyber risk management in accordance with NIS-2
An international industrial company, together with the AON Cyber Advisory transformed its cyber risk management - the goal: a scalable, efficient and auditable process for assessing the supply chain according to NIS-2 to establish.
With over 1,500 employees and several locations in the EU, the manufacturer is one of the top suppliers in its industry. In view of increasing regulatory requirements and growing dependencies in the supply chain, it was necessary to ensure a structured, traceable IT security audit of suppliers. The assessment was not only intended to create transparency, but also to provide verifiable documentation that could be used as proof of active IT security management. Supplier Risk Management serves. The process was set up and supported by the team of experts at AON, one of the leading providers of cyber solutions.
Challenge: Fragmented data, limited resources
The situation is equally challenging for all companies affected by NIS-2. Different maturity levels of suppliers and a widely varying understanding of cyber security - often characterized by the respective industry - make a uniform assessment difficult. In addition, not all accesses that entail potential risks are often known. Individual discussions quickly reach their limits here. At the same time, the pressure to meet the requirements of internal and external stakeholders, such as management, auditors and regulatory bodies, is increasing.
All in all, there is a lack of objective data for assessing cyber risks in the supply chain. Existing methods such as interviews or manual queries are extremely time-consuming and often limited in their informative value. In addition, there are not enough human resources available for a comprehensive assessment.
Short: For companies with hundreds or even thousands of suppliers, a comprehensible, scalable and efficient assessment methodology is needed to create transparency and systematically manage risks. The aim of the project was therefore to introduce a digital, scalable process that is both practical and compliant.
Solution: Hybrid assessment with intelligent technology
Procedure and project highlights
A standardized questionnaire with around 30 questions based on ISO 27001, NIST, C5 and IT-Grundschutz was developed to ensure a uniform and comprehensible assessment of the suppliers. The overall assessment was carried out in a hybrid process: via the digital questionnaire for self-disclosure, an automated, non-invasive vulnerability scan of the external attack surface and based on the technical assessment by the experts from AON Cyber Advisory. They also took over communication with the suppliers, analyzed the data received and prepared the results in a structured manner for internal reporting.
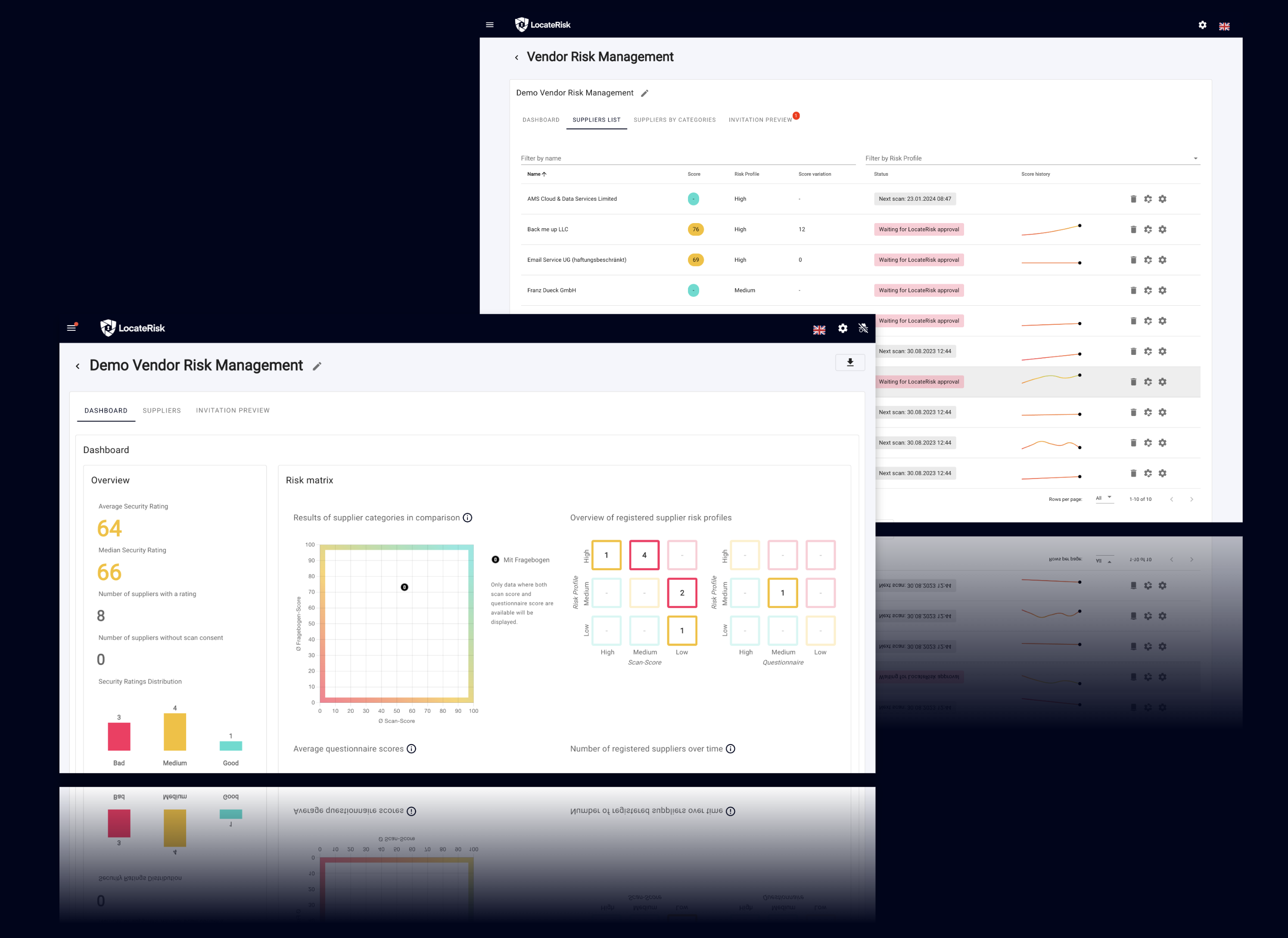
The technological basis of the project was the LocateRisk platform. It enables organizations to efficiently validate, monitor and compare the IT security situation of their suppliers and service providers. The combination of automated risk scans, digital compliance questionnaires and powerful comparison and management functions makes supplier risk management efficient, transparent and scalable. More about cybersecurity compliance mapping
A central element is the performance dashboard, which clearly visualizes all security-relevant information - such as criticality, IT risk score, compliance status and current changes. This makes it possible to identify potential risks from third parties at an early stage and address them in a targeted manner.
„Even our auditor expressly praised the procedure and emphasized that he wished other companies would adopt a similarly structured approach.“, emphasizes the manufacturer.
Important findings, but also hurdles in the course of the project
Some suppliers had to be specifically motivated and convinced in order to achieve active participation. The majority - around 60 to 70 % - were cooperative and willing to implement the requirements. A small number of suppliers were initially skeptical about the involvement of an external third party. In these cases, separate assurances were required to confirm participation.
Some suppliers were concerned that the non-invasive scan used could penetrate internal systems. However, as these are exclusively external IT security analyses that do not overcome any access barriers, these reservations were quickly dispelled. In the end, there were also some suppliers who refused to participate on principle - whether out of concern about disclosing their cyber security situation or due to internal company guidelines. These companies subsequently had to be classified as a critical risk, regardless of their actual IT security situation.
Interesting development in passing: After the project, an initially skeptical supplier decided to use the automated procedure to evaluate its own supply chain in the future - in preparation for its own NIS 2 strategy.
Efficiency, transparency and verifiability - the highlights of the project
The project impressed with its exceptionally high level of efficiency: Within just ten weeks, 50 suppliers were systematically evaluated. The average self-assessment via the digital questionnaire took less than 30 minutes per supplier.
A comprehensive overall report was prepared for the manufacturer, which bundled all relevant findings on the suppliers' cyber security situation. It contained clear recommendations for prioritization, such as which suppliers should be dealt with in greater depth in the short term. The suppliers themselves also benefited: each company received an individual evaluation with personal results and specific recommendations for improvement.
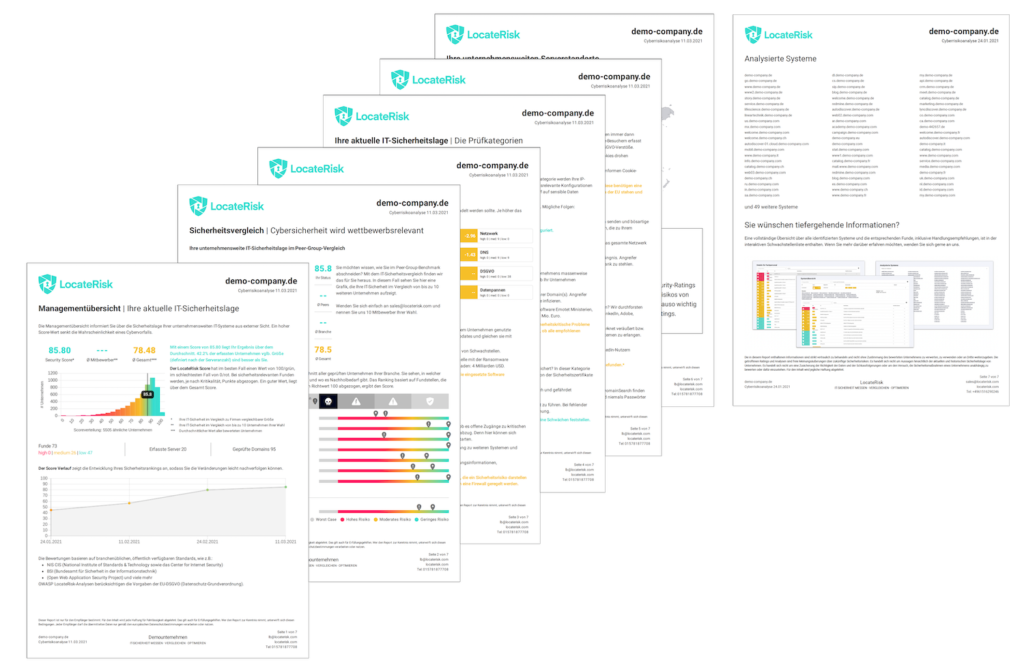
The results were presented visually - in the form of clear graphics and a matrix that allowed a quick assessment and comparison of the IT security situation. This provided a clear picture of the IT security level of the evaluated suppliers.
Particularly relevant with regard to risk avoidance: As part of the evaluation, suppliers with system access that posed an increased risk were identified. In these cases, targeted discussions were held with the responsible persons and access rights were restricted until a higher level of IT security could be demonstrated. More about IT risk analysis
Results and added value
- Time saving: Over 70 % reduction in effort compared to manual procedures.
- Technical validation: Combination of questionnaires with automated, non-invasive vulnerability scans.
- Risk management: Strengthening internal governance through a risk-based approach to supplier evaluation.
- Connectivity: Sound database for targeted follow-up projects such as safety discussions or contract adjustments.
In addition, the underlying methodology fulfills important regulatory requirements and serves as verifiable proof of active third-party risk management - for example in the context of the NIS-2 Directive.
Conclusion and outlook: An efficient model for more resilient supply chains
In view of increasing cyberattacks via the supply chain, the requirements for its security are growing. Regulatory requirements such as NIS-2 and DORA require scalable methods to systematically assess IT security risks from third parties. This is precisely where the chosen approach comes in: It increases transparency through continuous, comparable supplier cyber risk assessments and contributes to greater resilience at the NIS-2 relevant production company and its supply chain with targeted recommendations.
Further added value became apparent in the context of the ISO 27001 certification. The supplier assessment carried out could be used by the manufacturer as documented evidence for the control and assessment of risks in the supply chain - in line with the requirements of the standard. The results reports and documentation were incorporated directly into the audit without any additional effort and contributed to the successful certification.

„This is how supply chain risk management works today: we have established a scalable process that not only saves resources, but also impresses auditors.“
- Florian Lange - Cyber Security Advisor at AON Cyber Advisory
Project successes: Efficient, scalable and connectable
- Up to 50 suppliers evaluated in 10 weeks instead of 12 months in the old procedure.
- Prioritize weak points: Clearly evaluated findings with CVSS classification.
- Simplify reporting: Management-compatible score indicators for monthly reports.
- Rate service providers: Objective database for partner audits and IT risk assessments.
Request your personal Live-Demo now
Identify and reduce your cyber risks through a comparable and understandable overview of your IT security. Let our experts advise you and find out how LocateRisk can help you solve your cyber risks.








