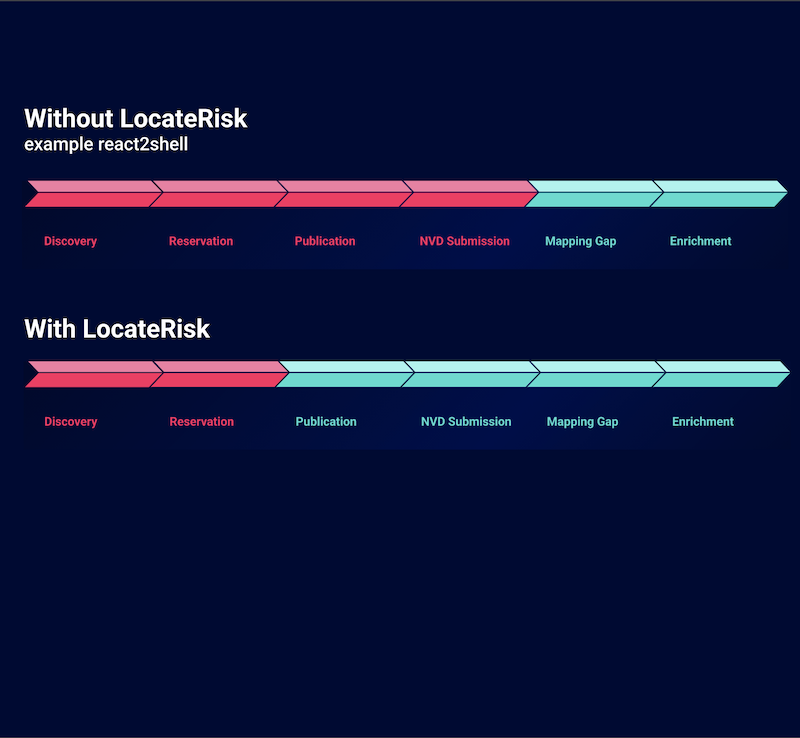
Preemptive intelligence - closing vulnerabilities faster
How to use preemptive intelligence to secure critical software as soon as it becomes known and shorten the time to action

„React2Shell“: Critical vulnerability in React & Next.js (CVE-2025-55182 / CVE-2025-66478)
„React2Shell“: Critical vulnerability in React & Next.js (CVE-2025-55182 / CVE-2025-66478) On December 3, 2025, a critical vulnerability in the React server components and the Next.js framework based on them was published. The vulnerability allows remote code execution (RCE), i.e. the execution of arbitrary code on affected servers, and potentially affects thousands of web applications worldwide. Particularly dangerous: The [...]
Supply chain attack on npm packages: What developers need to know
The vulnerable npm ecosystem npm is the heart of the JavaScript world. This is where developers exchange packages and build efficient applications. But it is precisely this openness that criminals are exploiting. Over 40 packages have been compromised. The attackers' goal: stealing data and manipulating build processes. The reach is particularly fatal. A single malicious package upload can affect widely dispersed projects and reduce software quality [...]

New Microsoft e-mail regulations: How to secure your business communication
The new Microsoft specifications offer the opportunity to comprehensively improve your cyber security.

LocateRisk is Best Cybersecurity Startup 2024 DACH
LocateRisk wins ATHENE Startup Award UP24@it-sa as Best Cybersecurity Startup 2024 DACH.

Excellent supplier risk management
LocateRisk awarded second place in WirtschaftsWoche's "Best of Technology Award 2024".
Supplier risk management made easy
Increase the efficiency of your supplier evaluations with automated workflows and processes.

Cybersecurity in the digital supply chain
This article provides you with an overview of the current status regarding GDPR, NIS2, DORA and CRA.

Cyberattacks on the supply chain
Cyberattacks on the supply chain can develop into avalanche-like damage scenarios. An overview of significant attacks and their effects.

DORA: Digital Operational Resilience Act
What DORA means, who it affects and where exactly LocateRisk can provide support.

New partner DATAGROUP on board
New in the LocateRisk partner network: We are very pleased about the partnership with DATAGROUP, one of the leading IT service providers in Germany.

Distr@l funding accelerates development of new security technology
Thanks to Distr@l funding from the state of Hesse, we are able to develop our new LR-Cont security technology. An accessible cyber security solution for companies of all kinds.

DIGITAL X 2023 - Be digital. Stay human.
We are at the start when Europe's leading digitization initiative brings together society, business and politics.

Funding Priority: Analysis of the Current State of IT Security
The NRW program "MID-Digitale Sicherheit" (MID Digital Security) subsidizes IST analyses that enable you to identify and close security gaps in your company.







